February 14, 2020, brought an unprecedented Valentine's Day surprise for Costa Rican police –– in a shipping container of decorative plants, they discovered 3.8 metric tons of cocaine.
Authorities said little about who was behind the record bust, which was intercepted in the Caribbean port city of Limón.
But not long after, Dutch police made another discovery: After breaking into the encrypted chat platform SkyECC, they found that a 41-year-old father of two had played a key role in the operation from behind his computer in the port city of Rotterdam.
On paper, Davy de Valk had struggled to hold down a steady job. Though he claimed to have studied computer science, Dutch prosecutors found he was living off social benefits, according to his indictment.
Yet the encrypted chats revealed that de Valk actually had regular — and well-paid — work as a “black hat” hacker, the term used for those who hack for criminal ends. His speciality was penetrating the IT systems of Europe’s major maritime ports and selling intel to cocaine smugglers.
To move their goods freely, criminal groups have traditionally had to corrupt a long chain of port personnel, from crane operators to customs inspectors. But the increasing digitalization and automation of shipping logistics has opened up new avenues for infiltration. With the information that hackers like de Valk can help provide, traffickers need little more than a single corrupt employee and a truck driver, experts say.
Using court records, police reports, and a cybersecurity analysis of de Valk’s hacking, OCCRP and its Czech member center investigace.cz have pieced together how he and his collaborators infiltrated the IT networks of Europe’s two busiest ports using methods that were, in some cases, relatively amateur.
A Dutch court found that de Valk was able to monitor how shipping containers were scanned at the port of Rotterdam, thereby helping his clients identify where to place narcotics to avoid detection.
He also breached the Antwerp terminal’s IT network through malware that was loaded onto a USB stick and inserted by a bribed office clerk, giving him access to data that could have allowed clients to pick up drugs without drawing attention, the court found.
De Valk charged hundreds of thousands of euros for his services, intercepted chats show. Yet his hacking methods were relatively basic.
“This is pretty low skill work,” Ken Munro, who runs a security consulting firm in the United Kingdom, told OCCRP after reviewing details of de Valk’s cyberattack at the Antwerp terminal.
“It’s a ‘noisy’ attack that would have generated plenty of alerts, had the Antwerp port systems been set up to detect these actions,” he added.
The inside view of de Valk’s hacking, which OCCRP is revealing in detail for the first time as part of the NarcoFiles, highlights how vulnerabilities at these ports have allowed them to become sieves for cocaine pouring into Europe at record rates.
In his defense, de Valk argued that he was doing undercover research to develop a video game about the drug trade, and only sold his criminal clients bad information. The court dismissed his explanation as “completely implausible,” and sentenced him in 2022 to 10 years in prison for crimes including unlawful hacking, as well as aiding and abetting cocaine trafficking.
OCCRP sent multiple emails and made multiple phone calls to de Valk’s legal representatives requesting comment — including about whether the conviction would be appealed — but received no response. It is not clear if he is currently serving his sentence.
Record Cocaine Busts
De Valk’s ‘Lines’
In the weeks leading up to the Costa Rica bust, de Valk outlined his services and price structure to clients over the chat platform SkyECC.
By monitoring the scanning history of companies that regularly shipped to Rotterdam, de Valk was able to tell which shipping lines were rarely probed and were therefore the best targets for secretly stashing cocaine, apparently unbeknownst to the shipping firms themselves.
If the container successfully reached Rotterdam, de Valk then helped clients retrieve their cargo by canceling the original pick-up service and forging transport orders, which would allow his clients to collect the container themselves, drive it out of the port, and comfortably unload the drugs. The total price for this package was 500,000 euros.
“You get a company that doesn't go through scan and your tp [transport] can pick it up without any problems,” de Valk wrote in one of the SkyECC messages cited in his court conviction.
De Valk referred to the reliable shipping companies he would recommend to clients as “my lines.”
For the haul intercepted in Costa Rica, he had recommended a container used by Vinkaplant, a well-known Dutch importer and exporter of tropical plants that makes regular trips to its fields in Costa Rica and other Central American countries.
“There are plants in it. Is easy to load. Isn't stuffed full,” de Valk wrote to his client, who was not identified by the court.
This mode of “piggy-backing” off a legal company is normally done without their knowledge. Vinkaplant was not accused of any wrongdoing.
Yet this time, de Valk’s “line” failed him. During a routine check, Costa Rican police noticed a suspicious discrepancy — the container’s weight did not match the figure that had been declared. An inspection found that in addition to 20 towers of ornamental plants, the container held briefcases containing 5,048 black packages, the majority of which contained pure cocaine.
PIN Code Fraud
Key to de Valk’s work would have been the ability to access the PIN codes of shipping containers.
These are unique reference numbers that are assigned to a container by a shipping company after its transport has been paid. In order to pick up the container at the dock, transporters must provide the correct code along with other documentation.
In 2018, authorities at the port of Rotterdam noticed a spike in reports of shipping containers being stolen, disappearing, delivered to the wrong address, or appearing in unexpected locations. Authorities realized that criminal networks had discovered a new modus operandi for drug smuggling, which Europol has dubbed “PIN code fraud.”
Traffickers had found that by illegally accessing the PIN codes of containers — through the help of corrupt port employees or by hacking — they could pick up the cargo by impersonating the transport company assigned to retrieve it. This data, as well as the container’s number, also allows them to follow the shipment’s status in the port, including when it is ready for release.
Without such codes, smugglers have had to resort to far riskier methods, such as sending a crew to break into the containers inside the port and flee with the smuggled goods. There have also been cases of “Trojan horse” containers, where extraction crews sneak into the port inside a container and wait, sometimes for days, until their shipment arrives and they have the chance to retrieve it.
The comparative ease of PIN code fraud means the data comes at a high price: encrypted chats show criminals have paid between 20,000 and 300,000 euros for such codes, according to the internal Europol report.
The large number of port and transport personnel who are able to view these reference numbers — in some cases up to 10,000 people in a single shipping company — provides traffickers with many targets.
“It's quite easy to find someone that has access to this code, and pay them money to get this,” said Rotterdam’s district chief of the seaport police, Jan Janse. “If you don’t say yes the first time, when you're in the shop doing your shopping, they’ll throw it into your cart again and maybe try a third time to offer you the money. There are [also] cases, of course, [where] then they tell people, ‘We know where your kids are going to school.’”
This type of corruption is the top method used by criminals to access internal information including PIN codes, he said.
De Valk’s chats make clear that he and his collaborators had access to inside information about the movement of containers at the Rotterdam port.
The Dutch court found that de Valk had fabricated a transport order, shared it with his collaborators, and canceled the legitimate transporter as part of his effort to arrange the consignment that was later stopped in Costa Rica. In a chat cited in the verdict, he sent an image of a transport order to his clients and wrote, “Under reference is the PIN code.”
In addition to that bust, de Valk was convicted of helping arrange a separate shipment of more than 200 kilograms of cocaine, which police found in Rotterdam in 2020 hidden in a shipping container of wine.
Investigators discovered encrypted SkyECC chats showing that de Valk had prepared a transport order and fake emails to facilitate the pick-up, using key data about the container provided by an unidentified member of a group chat, his conviction shows.
His indictment offered further details: De Valk and other members of the chat had allegedly accessed the port’s software for container management and, with the help of “possible corrupt port contacts,” had “direct insight into the container's entry, corresponding registration numbers and loading and unloading times,” prosecutors wrote.
The precise details of how they had accessed this information in Rotterdam are not known. But de Valk’s next adventure in Antwerp presents one possibility.
USB Hack
Days after the wine shipment was intercepted in Rotterdam, de Valk turned his sights on a new target with the help of a man named Bob Zwaneveld, according to their court convictions.
Zwaneveld, 57, did not embody the popular image of a crime boss. Before his arrest in 2021, he claimed to have spent seven years living in a camper van in a recreation park, prosecutors wrote in his indictment. Officially, he was unemployed aside from what he said was the odd construction job. Unofficially, he was actively involved in cocaine and arms trafficking, leading to a 12-year prison sentence in 2022.
OCCRP made multiple attempts to contact Zwaneveld through his legal representatives, asking for comment on the conviction and whether it would be appealed, but received no response. It is not clear if he is serving his sentence.
Chats show that Zwaneveld played a coordinating role in several drug deals in 2020, including arranging the sale to a U.K. friend of 100 “colos,” a term he and others used to describe kilos of Colombian cocaine. He was also having regular negotiations over encrypted chat platforms about the purchase, sale, or delivery of firearms, hand grenades, and ammunition.
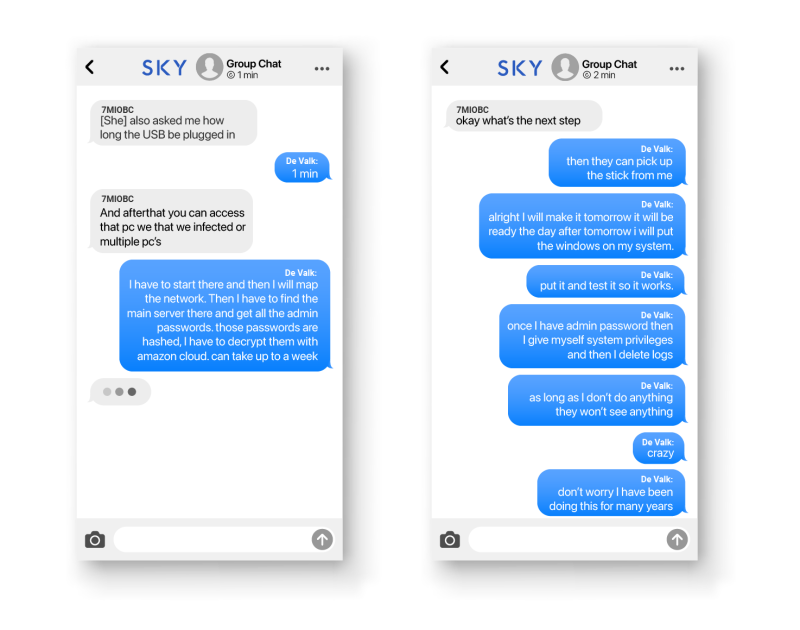
Together, Zwaneveld and de Valk planned to infiltrate the Antwerp terminal, which manages the second largest volume of shipping containers in Europe after Rotterdam, according to their convictions. To do so, they needed the help of someone on the inside — in this case, an office clerk stationed at the port.
The clerk told Belgian police she was approached by someone who offered her 10,000 euros to insert a USB stick into a computer at her workplace, according to testimony cited in de Valk’s conviction. After agreeing, she was given a SKY phone –– a secure device with the encrypted messaging app –– to communicate with a SkyECC account user identified in court only as 7MIOBC, who shared her queries in a group chat with de Valk and Zwaneveld.
The port employee was convicted in a Belgian court this March, according to local media. The reports did not give details of the conviction, or say whether it would be appealed. The employee did not respond to reporters’ requests for an interview.
Once de Valk finished preparing the USB stick, it passed through several hands, including Zwaneveld’s, before reaching the port employee.
“Just activate the program on the USB stick. double click and wait 15 seconds then you can take it out again,” de Valk instructed.
Soon, the operation was up and running.
“Yes, have it,” he wrote to the group chat, sending a screenshot revealing his access to the employee’s computer, with the word “user” displayed, followed by a photo of folders and drives. The user 7MIOBC replied with a photo of the USB plugged into the Antwerp terminal office computer.
After the port employee had opened the file on the USB and installed the malware, de Valk ran a series of “malicious activities” on the system, according to a forensic report of the hack carried out by the Dutch cybersecurity firm Northwave, which was cited in his conviction.
Chronology of a Hack
The Dutch cybersecurity firm Northwave analyzed de Valk’s September 2020 hack of the Antwerp port’s IT system, and investigace.cz obtained that report. Below is a timeline showing some of the cyber attacks de Valk ran on the system, according to Northwave’s investigation.
De Valk opened Antwerp’s container management program, Solvo, on September 21. Activity logs show that at 4am, he opened a user manual for the program, likely “to investigate what data they could obtain through Solvo (such as how to look up container locations),” Northwave wrote in its report.
The program would have allowed de Valk to see a wide array of information relating to staffing and the management and location of shipping containers. It would even allow him to generate PIN numbers himself, according to the cybersecurity firm.
Chats show de Valk also attempted to clone the ID badges of port staff. A few days later, he sent a picture to the SkyECC group chat showing a computer screen with the text “badge” and “alfa pass,” which refers to plastic cards that port employees use to access different areas of the facility.
“Think we will soon be able to create a card ourselves,” he wrote.
It is not known whether de Valk eventually managed to fabricate such IDs. The court did not note any evidence that de Valk was involved in trafficking attempts after his September 2020 hack, either. Yet there is evidence he was active on the Antwerp terminal’s IT system until at least April 24, 2021, according to Northwave’s investigation. (De Valk didn’t respond to requests for comment on the claims.)
The logs Northwave was able to recover suggest that de Valk accessed the Solvo container software multiple times between October 19 and April 24, 2021, visiting pages that monitored containers, vehicles, staff passes, and names of transport drivers.
While de Valk’s activity after this period is unknown, the prosecution noted that, based on a scan of his seized laptop, he continued to have “chat conversations with various people about transport modes and deck cargoes” until as late as August 2021.
‘Black Harbor’
The full extent of what de Valk achieved before his arrest in September 2021 is not known. But European police believe that he was part of a broader pattern of PIN code fraud that has enabled the trafficking of at least 200 metric tons of cocaine through Rotterdam and Antwerp since 2018.
When Belgian police started investigating the intercepted SkyECC chats, they were hoping to shut down what they referred to as the “black harbor” –– the chains of corrupted port employees, transport drivers and others who have made trafficking possible –– said Kurt Boudry, a senior officer with Belgium’s federal police.
But “we didn't know it was going to be so wide,” Boudry told OCCRP.
PIN code fraud is likely substantially underreported, according to a 2023 Europol report, and may be occurring at other European ports as well.
In some cases, after unloading their contraband outside the port, the transport drivers working with drug traffickers will continue onwards and deliver the container to its rightful importer, meaning some cases are never detected or reported, the report says.
Janse, the Rotterdam seaport’s district police chief, said the biggest battle against traffickers is their ability to corrupt ports using money and intimidation.
Port authorities and shipping companies are experimenting with ways to tighten security, including by offering training to staff and by limiting the number of people who have access to data that can be exploited by traffickers, he added.
“I'm not saying that we are going to win this war, but I am saying that we are able to make it more controllable,” Janse said.
Additional reporting by Brecht Castel (Knack) and Interferencia de Radios UCR