In October 2020, Maxim Karpenko, an independent Russian mobile game developer, was sitting on a train about to go on vacation when a friend messaged him with troubling news.
Stavrio Ltd., a little-known company in the U.K., had just filed for a trademark to Karpenko’s most prized work, WorldBox, a “god simulator” mobile game that allows users to create and nurture virtual civilizations.
Karpenko had spent eight years developing WorldBox, which had been downloaded millions of times. Now it looked as though he might lose everything overnight. Stavrio Ltd. had quietly replicated the game and was offering it on mobile app stores under its own name.
“I panicked and cancelled the trip, went back home … and started looking for lawyers,” Karpenko told OCCRP and its Estonian partner, Eesti Ekspress.
Karpenko remembered meeting Aleksandr Novikov, a mobile game executive affiliated with Stavrio Ltd., at a game industry conference in Minsk, Belarus, a year earlier. Novikov stood out because he was wearing a suit in a space where t-shirts, jeans, and hoodies were a far more common sight. He introduced himself as an investor in JustMoby, a mobile app publishing company based in the southwestern Russian city of Tolyatti.
Novikov kept in touch with Karpenko and eventually made a six-figure offer for WorldBox. Unsure about Novikov’s sincerity, Karpenko declined.
Now, with his game seemingly stolen and his future plans in tatters, Karpenko was determined to learn more about Stavrio Ltd. In November 2020, Karpenko published a Reddit post about several other apps that Stavrio and other companies connected to Novikov had passed off as their own.
A month later, Karpenko received a phone call from an unknown Russian number, and a man speaking Russian told him that he had three days to remove the online posts. “He told me he was asking nicely or there were going to be consequences,” Karpenko told OCCRP.
Twenty minutes later, Karpenko received a text message with his relatives’ car license plate numbers and home addresses. He filed a report with Russian police, seen by OCCRP, but he still doesn’t know who was behind the message.
Karpenko then received a letter from a law firm representing Novikov and Jigsaw Puzzles LLC, a Russian mobile app publisher. Renamed JustMoby in December 2020, Jigsaw Puzzles LLC had been founded in 2018 after Adeco Systems, a company linked to Novikov, was liquidated.
The letter threatened legal action unless Karpenko removed his online posts. Karpenko refused, and Novikov sued him for libel. In a separate case, Karpenko is disputing the trademark claims over WorldBox.
But what he didn't know was that he had stumbled onto a much broader and more sophisticated money-making operation than just the theft of one app.
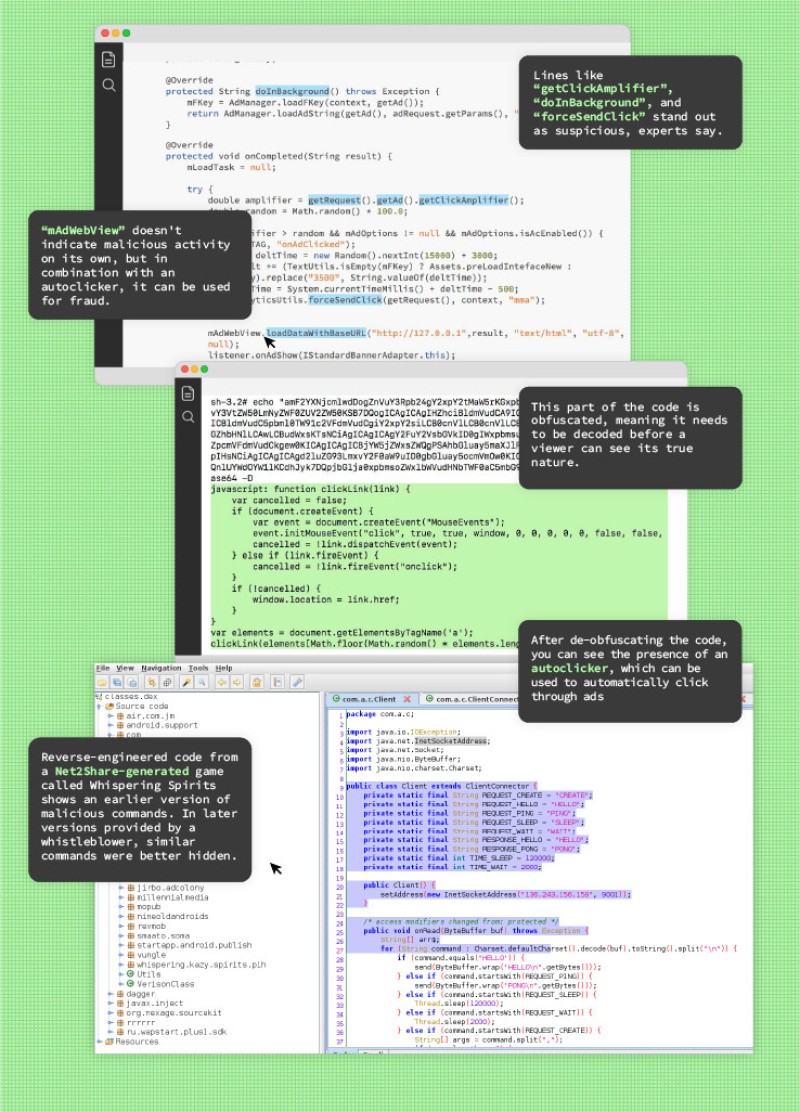
Drawing on interviews with four former employees and an analysis of leaked software code, OCCRP found that more than 20 companies around the world connected to Novikov and his firms created and disseminated mobile apps, including many outright copies of existing ones, infected with malware that artificially generated ad revenue.
In total, mobile apps developed by JustMoby, Adeco, and related publishers were downloaded almost 80 million times from mobile app stores like Google Play and Apple’s App Store. In many cases, the same apps were marketed under different mobile app publishing company names.
After infecting users’ phones with “trojan” malware, the apps connected to JustMoby and Adeco deployed a variety of techniques, such as spamming fake ad-views and spawning invisible browsers on infected phones without the user’s knowledge, thereby generating what may have amounted to millions in fraudulent revenues. As of 2019, none of the apps appeared to be deploying trojans, but they continued to include software experts say could be used for digital advertising fraud.
Deceptive behavior meant to pump up digital ad revenue is a booming illicit industry. Cybersecurity firm CHEQ estimated losses from digital advertising fraud hover around $35 billion per year — overtaking even credit card fraud, according to a 2019 report.
Contacted by OCCRP, Novikov denied stealing Karpenko’s work, distributing ad fraud malware, or having any connection to most of the mobile app publishing companies that OCCRP has linked to him.
“Neither my company, JustMoby, nor me personally, are in any way interested in short-term profits of any kind, particularly if those are generated by misleading advertisers and partners. We never employ such methods in our work,” Novikov said.
Novikov’s Network
The web of companies linked to Novikov — mapped first by Karpenko and then OCCRP — spans Estonia, Latvia, the Czech Republic, and the U.K. Their exact ownership structure and financial status is often difficult to confirm.
Malware Injection
In 2015, Russian-language tutorials began appearing on YouTube, Facebook, Twitter, and niche forums, blogs, and websites showing how Net2Share, a software tool developed by Adeco Systems, could be downloaded and used even by someone with zero programming skills to clone mobile apps. All a user had to do was download a regular mobile app, replicate it in Net2Share, and upload the duplicated copy to app stores. In exchange, they would get a cut of the revenue earned from ads displayed by the cloned apps.
But Net2Share had a hidden feature that even its ethically dubious users didn’t know about.
A former Adeco employee, who spoke on condition that he be identified only by the pseudonym “Sergey,” told OCCRP that every mobile app cloned by Net2Share was also infected with malware that secretly spammed phones with huge amounts of fake traffic, artificially pumping up ad viewership numbers.
Sergey provided OCCRP with original software code written by Adeco developers, which showed clear evidence of malware. Developer notes with Adeco employees’ email addresses helped to establish that the software code came from Adeco. The volume of the code — nearly 5,000 files, amounting to over half a gigabyte, shared along with a detailed history of changes via the version-control system git — means they would have been difficult to fake.
Adeco has previously been suspected of distributing this type of malware. In 2018, the cybersecurity blog Ars Technica published an article about the so-called Dresscode botnet — a pervasive form of malware that automatically runs on a network of devices — that appeared to have infected millions of mobile phones through hundreds of apps installed from 2016 to 2018.
An anonymous hacker who infiltrated the Dresscode botnet claimed to Ars Technica it had accessed more than four million phones to generate some $20 million in fraudulent ad revenue. Data uncovered by the hacker showed that one or more people with control over the adecosystems.com domain were actively maintaining the botnet.
Ars Technica contacted Lookout, a security intelligence research consultancy, for independent confirmation of its findings. Christoph Hebeisen, the director of Lookout security intelligence research, wrote extensively about the Dresscode botnet, and like Ars Technica, also connected it to Adeco’s domain.
Hebeisen told OCCRP that he believes Adeco was benefiting from the Dresscode botnet because infected devices opened connections to third-party Internet addresses that exclusively connected to Adeco ad servers to simulate ad views on mobile devices.
After the 2018 reports by Ars Technica associating Adeco’s name with a malicious botnet, Adeco was liquidated and Jigsaw Puzzles LLC was incorporated. In December 2020, Jigsaw Puzzles changed its name to JustMoby, the name of an Adeco partner company in Belarus.
Novikov told OCCRP that malware was detected in some Adeco apps because Adeco itself had been hacked.
“To the best of my knowledge, in 2016, the Adeco Systems infrastructure suffered a massive hacking attack. As a result, malicious web applications were deployed on several advertising servers,” Novikov said.
Cybersecurity Review
When Ars Technica first published its report, Adeco officials denied their involvement. But in addition to Sergey, two former Adeco employees interviewed by OCCRP said they suspected that the mobile apps they worked on were embedding malware when they began receiving alerts from antivirus engines.
To verify their suspicions, OCCRP asked an engineer at Estonian cybersecurity firm CybExer Technologies to review software code used in Adeco apps and a software development kit that Sergey provided to OCCRP. Software development kits, known as SDKs, are packages of software tools used to build mobile and web applications.
The engineer, Egils Malbergs, also independently downloaded and reviewed a mobile app cloned with Net2Share and six mobile apps published to Google Play by companies that appeared to be connected to Adeco.
Malbergs did not find malware in the Google Play mobile apps, but he confirmed that the software code and the mobile app cloned with Net2Share both contained malware. According to Malbergs, the Net2Share-cloned app could access infected phones to spam ad networks whenever it pleased, and some of the software code provided by Sergey contained malicious code found inside Net2Share-cloned apps.
When shown screenshots of the malware code that Sergey said originated from Adeco, Novikov said he didn’t know what the code did or whether it originated from his developers. Saying that he had his own experts review the screenshot sent to him by OCCRP, Novikov said the code wasn’t malware but appeared to be for collecting analytical data.
Adeco’s SDK, dubbed Inappertising, was also shown in Malbergs’ analysis to spawn invisible browsers that channeled fraudulent ad interactions, such as impressions and clicks, to popular ad networks like Twitter’s MoPub and Google’s AdMob.
Because SDKs are marketed to app developers, they are a common method of transmitting malicious code to as many mobile devices as possible, Geoffrey Cleaves, managing director of mobile anti-fraud company Secure-D, told OCCRP.
OCCRP also downloaded all the apps connected to Adeco Systems and JustMoby it could identify on Google Play, and uploaded them to VirusTotal, a tool used to detect malware. The results showed that 28 of the apps connected to Adeco Systems or JustMoby, and three apps marketed under Jigsaw Puzzles LLC, had currently or previously implemented the Inappertising SDK. Some of these apps — which were collectively downloaded at least 7 million times — were removed from Google Play during the investigation.
OCCRP provided the list of apps to an analyst at Lookout, Arezou Hosseinzad-Amirkhizi, who confirmed that the version of the SDK provided by Sergey was present in at least 14 games available on Google Play. Given that the SDK would be updated occasionally, different versions of the software could be available.
Hosseinzad-Amirkhizi said that the code was capable of parsing all the links within a received page and automatically clicking on a random link each time. “This version could potentially be click fraud, depending on what is served to it by the servers,” she said.
Two days after OCCRP contacted Novikov with questions about the Inappertising SDK, servers supporting it went offline. Novikov claimed that he did not know about, or help to deploy, any Inappertising SDK in JustMoby and Jigsaw Puzzles LLC mobile apps.
Booming Business
OCCRP found that 22 other mobile app companies registered in different countries shared corporate formation dates, corporate proxy registrant services, partners listed on websites, IP addresses, or digital certificates with Adeco, JustMoby, or their apps. Altogether, these companies published at least 200 apps on Google Play, where they were downloaded more than 76 million times, and on the Apple App Store, which doesn’t disclose download numbers.
Novikov denied being affiliated with any of these app companies other than Adeco, JustMoby, or Jigsaw Puzzles, claiming they were independent publishing partners.
However, nine of them listed Egor Agafonov, a Latvian man whom Sergey refers to as a lawyer for Novikov’s companies, as CEO or owner, according to corporate registries.
Agafonov confirmed to OCCRP that he was a “business partner of Aleksandr Novikov,” but said he mostly dealt with financial issues. He claimed to not know much about mobile apps published by the nine companies that list him as CEO or owner, and which Novikov claimed were independent from JustMoby.
Former employees of Adeco Systems and JustMoby said that app stores repeatedly banned them for cloning mobile apps, making it necessary to work through many different companies. “If Google Play banned some accounts, we made a new company for a new account,” Sergey told OCCRP.
Still, despite the bans, Novikov’s sprawling network of invasive mobile apps appears to be thriving. The most popular game by Novikov’s mobile app publishing companies, Raft: Ocean Nomad, has been downloaded more than 50 million times.
As with Karpenko’s WorldBox, Raft: Ocean Nomad is virtually identical to Raft, a desktop game developed by Sweden-based RedBeet Interactive. RedBeet declined to comment.
Novikov said he and a team of former colleagues from Adeco Systems who developed Raft: Ocean Nomad had started working on it in 2016 before RedBeet, but two former Adeco Systems employees contacted by OCCRP said that was untrue.
Raft: Ocean Nomad is now popular enough that it generates up to $800,000 per month in revenue. There is no indication that the current version of Raft: Ocean Nomad employs malware — although, until February 2020, the game carried Inappertising SDK functions.
OCCRP contacted one of the official owners of a mobile app company in the international web of firms related to JustMoby and Adeco Systems. The man confirmed — while asking for anonymity — that he had been asked by Novikov to be the official director and owner of the firm, which earned millions of euros in profits in 2019 and 2020.
The man claimed he hadn’t benefited from any of the revenue that flowed through the company.
“No,” he answered. “If these were my companies and games, I would be a rich person.”