A recent report from Microsoft’s Security Response Center identifies five different ways such accounts can be hacked, with the distinguishing feature “that the attacker performs some action before the victim creates an account at the target service.”
Researchers analyzed 75 online services and found that at least 35 ― including Instagram, LinkedIn, Wordpress, Dropbox, and Zoom ― were susceptible to this type of hack.
The security weaknesses were reported to the respective organizations, with the findings “already acknowledged as being of high severity by a major video conferencing service,” who were given 90 days to address them before Microsoft published its report.
Andrew Paverd and Avinash Sudhodanan, authors of the study, told OCCRP on Thursday the aim of their research was “to raise awareness of these potential vulnerabilities and to help organizations and individuals defend against them.”
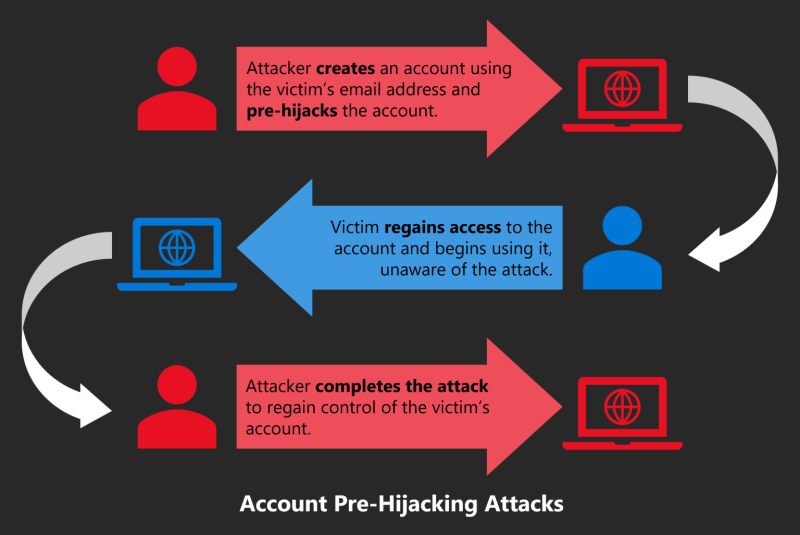
The basic process behind pre-hijacking attacks takes place in three stages. First, the hacker creates an account with an online platform using the victim’s personal details, likely an email address or phone number obtained from a data breach at another website.
The attacker then either tricks the victim into using those details to sign up ― or rather, sign in ― with the platform, or simply waits for them to do so. Finally, the hack is completed when the attacker secures exclusive access to the victim’s newly-created account, or continues to access the account at the same time as the user.
According to the report, it is important for hackers to be able to anticipate which websites their victims are likely to sign up for in future. But researchers noted that this kind of activity can also be significantly scaled up, with wider attacks requiring less targeted profiling given the likelihood that at least some people or organizations will fall victim to this kind of activity.
In 2018, a study by the University of Maryland suggested that hacking attacks around the world take place at an average rate of one every 39 seconds. Last year, U.S. network operator Verizon reported that more than 80% of such attacks are likely to be financially motivated, while tech conglomerate Cisco estimates more than half of small companies go out of business within six months of suffering a cyberattack.
Paverd and Sudhodanan recommended that users enable multi-factor authentication, such as two-step verification, as this represents the best defense against pre-hijacking attacks.